In this blog, we explain the latest phase in the NHS’ programme of direct engagement with its suppliers, announced in an open letter in January, and outline what this means for organisations working with the health sector. We explore why cyber resilience is becoming increasingly critical, and provide practical guidance on how suppliers can prepare for future engagement and strengthen their overall security posture. We also highlight the key measures suppliers are encouraged to adopt, as well as breaking down the role of the Data Security and Protection Toolkit (DSPT).
In January 2026, NHS England and the Department of Health and Social Care issued an open letter to around 36,000 NHS suppliers across the entire supply chain. The message was simple but urgent: rising cyber attacks were putting patient care and core NHS services at risk, and every supplier (whether clinical, non clinical, digital, estates, equipment, or service based) had a role in strengthening defences. The letter stressed that cyber security was no longer just a technical issue for IT companies; any supplier with access to NHS systems, data, or infrastructure could become a weak link. To address this, the NHS announced it would introduce more direct checks and stricter expectations to ensure suppliers met required security standards. The overall aim was to create a more resilient, joined up approach to protecting the NHS from cyber threats and safeguarding patient safety.
The letter explained that the NHS will now move on to the next phase of its programme of direct engagement with suppliers. The previous phase involved asking suppliers to voluntarily sign up the Cyber Security Supply Chain Charter, an NHS initiative of best practice.
This open letter aligns with wider ongoing Government initiatives, including the recently published Government Cyber Action Plan, which was released on the same day that the Cyber Security and Resilience Bill underwent its Second Reading. To learn more about the Bill, read our blog Cyber Security and Resilience Bill Policy Statement – What to Expect.
What does the programme of direct engagement involve?
Beginning in January 2026, NHS England or a relevant contracting authority may reach out to an NHS supplier to discuss its cyber security controls, including measures outlined in the Supply Chain Charter. They may also request additional details or evidence if extra assurance is required, such as when a supplier supports critical or when early conversations or risk indicators suggest that further assurance would be beneficial.
Whilst this remains voluntary, it highlights the NHS’ increasing scrutiny on the cyber security and resilience of its supply chain.
Why does the programme matter?
Cyber attacks now represent one of the most persistent and damaging risks facing organisations across every sector, and the UK is experiencing a steep escalation in both frequency and severity of incidents. Healthcare is no exception, with recent years having seen a number of NHS suppliers and healthcare organisations suffer major attacks.
For this reason, organisations should now approach cyber attacks as a matter of when, not if, ensuring the implementation of appropriate security and resilience measures to protect against, detect, respond to and recover from cyber incidents. Implementing the controls in the NHS Supply Chain Charter should therefore be seen as a minimum standard, not only to strengthen NHS confidence in your organisation, but also to protect your own systems, data, services and operational continuity.
How can suppliers prepare?
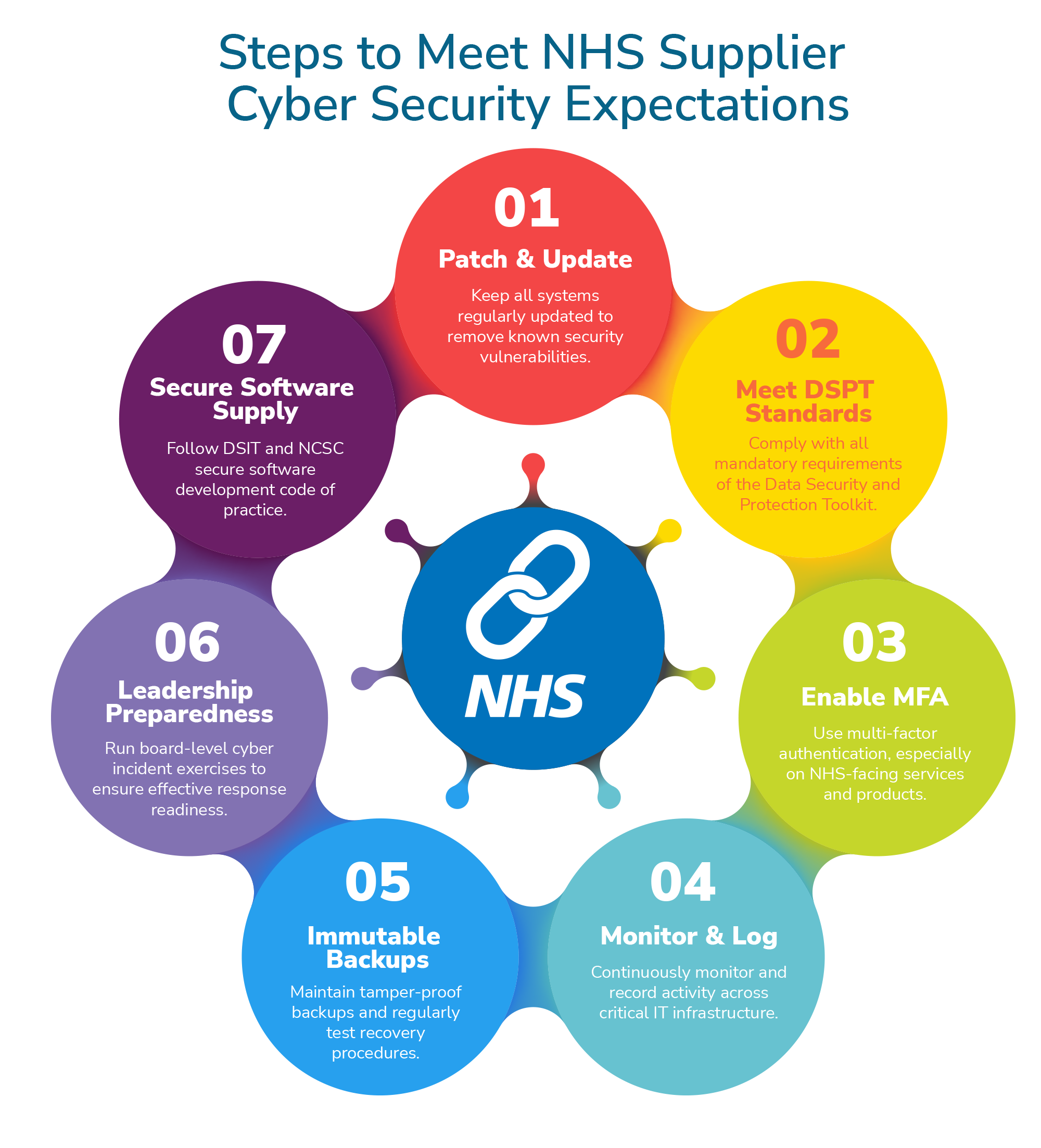
In its letter, the NHS recommended that suppliers review the expectations defined in the Supply Chain Charter to prepare for these discussions. These expectations include:
- Ensuring systems are patched against known vulnerabilities
- Meeting all mandatory requirements of the Data Security and Protection Toolkit (DSPT)
- Applying Multi-Factor Authentication (MFA) and enabling it on NHS-facing products where appropriate
- Deploying effective continuous monitoring and logging of critical IT infrastructure
- Ensuring backups that cannot be changed, and having tested recovery plans
- Conducting board-level exercising to ensure cyber attacks can be responded to
- Following the Department for Science, Innovation and Technology (DSIT) and National Cyber Security Centre (NCSC) Software Code of Practice when supplying software.
What is the DSPT and how can the requirements be met?
The DSPT is an online self-assessment tool that enables suppliers to the NHS to publish their performance against ten data security standards.
- Personal confidential data
- Staff responsibilities
- Staff training
- Managing data access
- Process reviews
- Responding to incidents
- Continuity planning
- Unsupported systems
- IT protection
- Accountable suppliers
To ensure these standards are being met, it is important to gain a thorough understanding of what specifically is being asked of your organisation. For example, one of the elements required to meet standard 6 (Responding to incidents), is to have antivirus or malware protection installed.
Once your organisation understands the exact measures that need to be in place, you can then conduct an audit or gap analysis to determine which requirements are already being met, and what actions are required to implement outstanding requirements.
Conclusion
The letter from the NHS, along with the overarching Government Cyber Action Plan, reinforces the UK Government’s ongoing commitment to increase the cyber resilience of the supply chain, with a particular focus on the resilience of the health sector. As the UK Government moves towards direct engagement with suppliers to discuss controls and request evidence, the direction of cyber resilience expectations is clear: suppliers should be demonstrating stronger, more mature security practices as a routine aspect of their work with the NHS.
How Can URM Help?
With extensive experience supporting organisations’ conformance to a range of security standards and frameworks (such as ISO 27001, Cyber Essentials, and the PCI DSS), URM is ideally positioned to help you strengthen your organisation’s resilience and ensure that you meet the standards set out in both the Supply Chain Charter and DSPT.
As an Assured Service Provider under the NCSC Cyber Incident Exercising (CIE) scheme, URM can assist you in practising, evaluating and improving your cyber incident response plans in a safe environment by developing and delivering cyber incident exercises in either a ‘tabletop’ or ‘live-play’ format. Conducting such exercises will help you to both satisfy the exercising expectations of the Supply Chain Charter, and ensure your organisation is in the best position possible to recover in the event of an attack.
In addition to cyber incident exercising, URM can provide holistic business continuity consultancy services and guidance that are informed by practical experience and recognised best practice. To conduct an effective business impact analysis (BIA), we can provide BIA support where we work with you to establish your BIA methodology, as well as our BIA tool, Abriska® 22301, which simplifies the BIA process and helps you create your business continuity plan (BCP). With the BIA in place, URM can help you produce and implement bespoke BCPs or incident management plans (IMPs), which are always developed with your organisation’s unique needs in mind. We can also offer tailored BC exercise services where we devise challenging, bespoke scenarios to exercise your plans and provide a report on your team’s response, including any improvement recommendations.
Meanwhile, as a CREST-accredited provider of penetration testing, URM can offer a range of pen testing services to identify the vulnerabilities affecting your environment and assets before they can be exploited by a threat actor, thereby reducing the risk of a breach. For example, we can offer network and infrastructure penetration testing against all IP addresses associated with your organisation, location or service from either an internal or external perspective. We can also conduct cloud penetration testing, web and mobile app testing, as well as business-led pen testing, where the scope of the test is determined by your organisation’s unique issues and concerns.
URM is pleased to provide a FREE 30 minute consultation on penetration testing for any UK-based organisation.
If you are unsure, URM can perform CREST-accredited internal and external penetration testing against all IP addresses associated with your organisation, location, or service.
Designed to assess the architecture, design and configuration of web applications, our web application pen tests use industry standard methodologies to identify vulnerabilities.

URM’s blog discusses the best next steps your organisation can take following Cyber Essentials certification to further enhance its security posture.

URM’s blog offers advice on answering questions in the Cyber Essentials SAQ which relate to access control, admin accounts and authentication methods.

URM’s blog explores common weaknesses in organisations’ security programmes, & outlines practical, cost-effective measures to reduce the likelihood of a breach



