This blog unpacks the foundations of information security risk by exploring its core components (assets, threats and vulnerabilities) and showing how they combine to create meaningful risk scenarios. It explains how organisations can use impact and likelihood scales to quantify risk, and how tools such as risk matrices and RAG ratings help determine which risks fall within or outside an acceptable appetite. We also examine how different risk types influence prioritisation and why a clear, well defined treatment strategy ensures that resources are focused where they deliver the greatest benefit. Ultimately, the blog provides a practical framework for understanding, valuing and managing information security risks in a structured, proportionate way.
Following the completion of an information security risk assessment, you may be presented with a substantial list of identified risks. This typically raises two questions: whether you need to address all of them, and how should you prioritise the risks to ensure the most critical ones are dealt with. Few organisations have unlimited resources, and attempting to tackle every risk simultaneously can quickly deplete those resources, leaving important risks unaddressed. As such, you need to have a clear understanding of which risks matter most and need to be dealt with as a priority.
What is Risk?
Before exploring the fundamental questions raised above, it is useful to step back and consider a more basic one: where did these risks come from in the first place?
Put simply, risk is the ‘effect of uncertainty on objectives’. Risks may be positive or negative, with positive risks representing opportunities that can be leveraged. However, most risks faced by organisations involve potential negative impacts on their objectives and therefore need to be managed in a way that reduces their likelihood or makes their consequences more acceptable. From an information security perspective, this means focusing on the potential adverse effects that threats and vulnerabilities could have on your information assets.
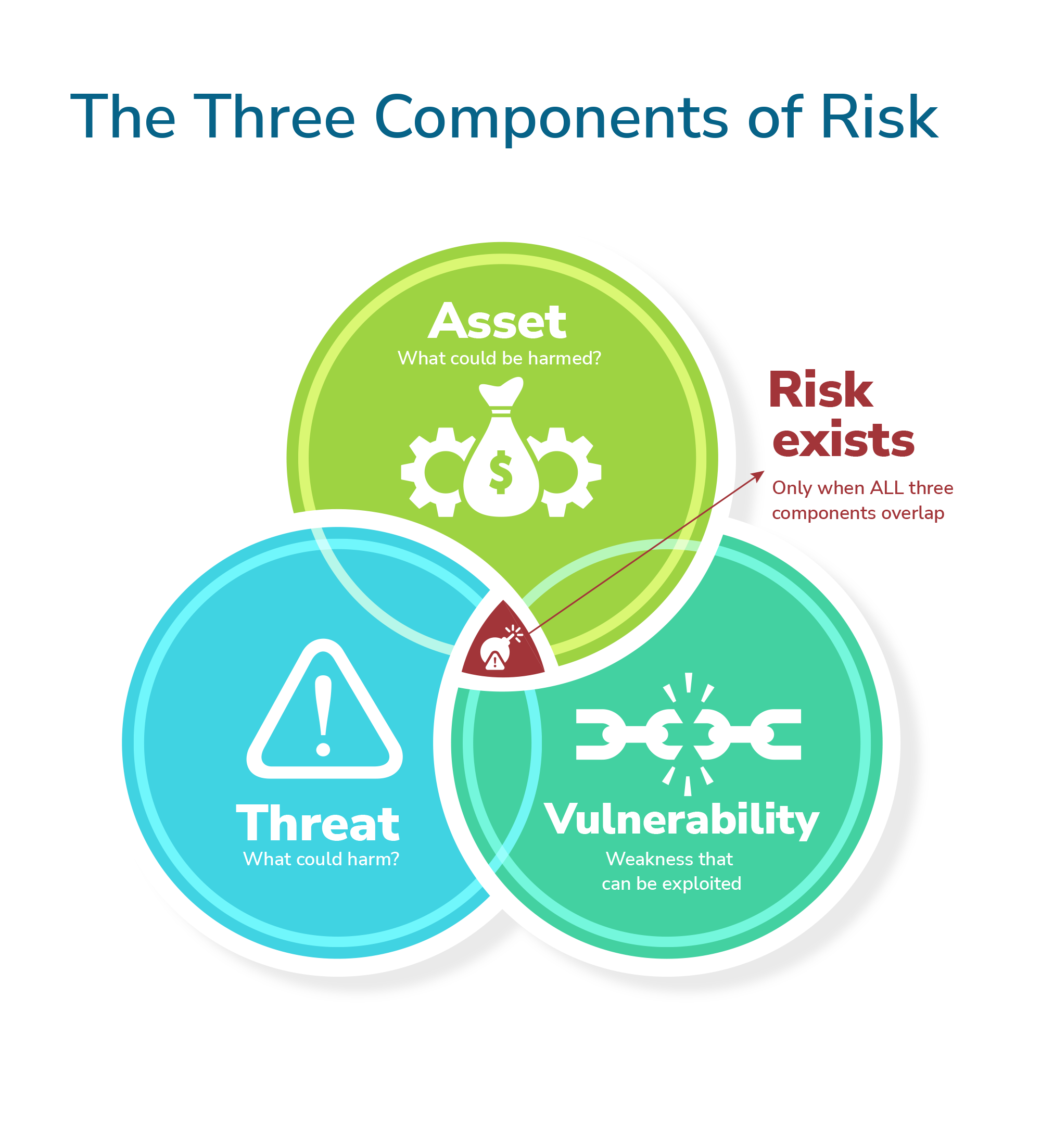
For risk to exist there must be three components present.
The first component is the asset, and risk is concerned with the impact on the organisation should that asset be compromised. In the context of information assets, the impacts could be associated with a breach of confidentiality, integrity or availability (CIA). To learn more about these concepts, read our blog What is the CIA Security Triad? Confidentiality, Integrity and Availability Explained.
The second component is the threat, which is the entity, event, or action with the potential to cause harm. A threat is essentially anything (can be deliberate, accidental, or environmental) that could exploit a weakness and negatively affect the asset.
The third component is the vulnerability. This is a weakness in either the asset itself or, more likely, in a supporting asset used to store, process or transmit the asset. When the security of an asset or supporting asset is weak, that vulnerability can be exploited by one or more threats, resulting in harm to the organisation.
What is the Value of Risk?
Once you have identified all three components, you can begin to consider how you might ascribe a value to the risk. This is achieved through a simple calculation where you multiply the impact value by the likelihood that the threat will exploit a vulnerability and cause harm to the asset.
Scales are normally used for this process. For example, you may apply a simple 1-5 scale to determine the level of impact, with higher numbers representing a greater perceived impact resulting from a compromise of CIA.
You can also use a 1-5 scale for likelihood. When determining the likelihood value, you consider the information about the threat itself together with your knowledge of any associated weaknesses to then plot the threat on your scale.
Finally, multiplying the impact and likelihood scores provides an overall risk value. Repeating this for each identified risk enables you to prioritise them based on their numerical ratings.
Risk Treatment Strategy
In addition to using numerical values to establish risk priorities, it is also important to consider the type of risks you are dealing with. Risk type is directly associated with the nature of the potential impact on your information assets. For example, you might determine that risks resulting in a loss of availability, such as a system outage that disrupts critical services, carry more weight for your organisation. Alternatively, you may consider risks involving non-compliance with information-related legislation or regulatory requirements, or those with significant financial or reputational consequences arising from a security incident, to be the highest priority. A PESTLE analysis (political, economic, social, technological, legal, environmental) can be a useful tool for identifying which categories of risk are most significant for your organisation. Once you have determined what’s most important and how you will prioritise your risks, either through numerical value or type (or a combination of both), this forms the basis of your risk treatment strategy.
Risk Appetite
To determine how to prioritise the risks that need to be addressed, you also need to understand your risk appetite. Risk appetite refers to the amount and type of risk that your organisation is willing to tolerate or accept.
As outlined above, you can prioritise risks by their value (amount), as well as the impacts associated with the risks (type). But the question remains: at what point does a risk become unacceptable?
A risk matrix can be useful here. The matrix is derived from the scales we discussed earlier; in this case, a 1-5 scale for both impact and likelihood. By transferring these scales into a spreadsheet or similar format, you can plot each risk according to its impact and likelihood values. This creates a grid within the spreadsheet of 25 cells (with 14 possible values*) in which a risk may fall. For example, a risk with a likelihood rating of 4 and an impact rating of 2 would be placed in the corresponding cell, which has a value of 8 (impact 2 x likelihood 4 = 8).
*Can’t get to some numbers by multiplying 2 sets of 1-5 by each other, e.g., 7, 11, 13, etc.
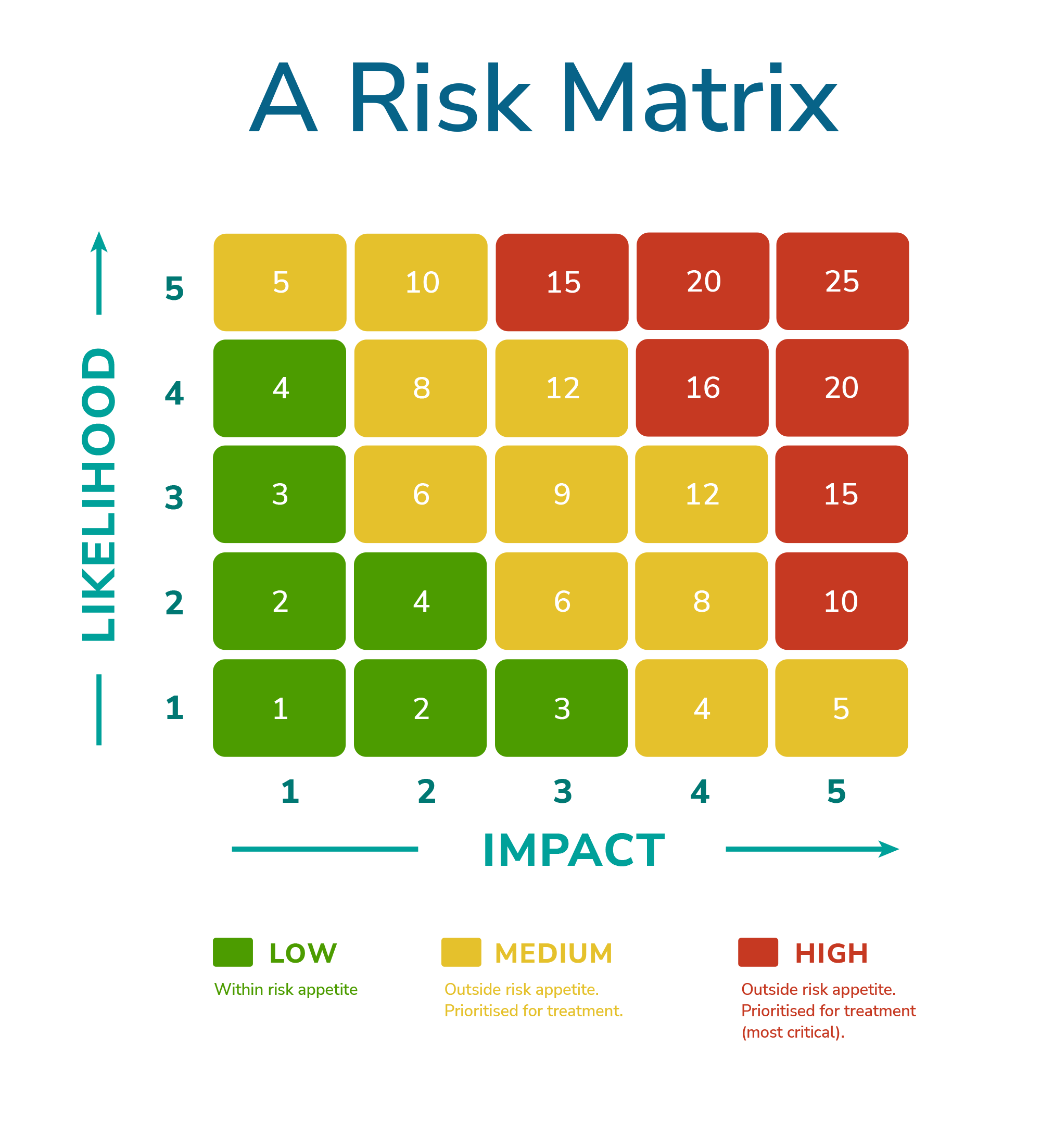
Within the matrix, you can apply a red, amber, green (RAG) status to each cell. Cells that score below a defined threshold and are considered a low risk would be coloured green, whereas high risks with a score that exceed your upper threshold would be coloured red. Risks that sit between these two boundaries would be coloured amber.
The cells that are designated as green represent risks that fall within your risk appetite. Any risks outside your appetite, i.e., amber and red risks, would be prioritised for treatment, with red risks being higher priority and requiring the most urgent attention.
However, it’s important to continue considering risk type when determining treatment priorities. Your risk treatment strategy may, for example, have specified that risks relating to confidentiality breaches take precedence over all others, so even if you identify red risks, an amber confidentiality-related risk may still be addressed before higher scoring risks of other types.
Addressing All Risks
So far, we have addressed one of the two fundamental questions raised at the beginning: how to prioritise risks. The remaining question is whether you need to address all identified risks. The short answer is yes; however, by using the risk matrix, you may find that a significant portion of the risks you’ve identified will fall within your defined risk appetite. These risks can be accepted, which means no further treatment is required at this stage. They simply need to be monitored to ensure they don’t become more significant and shift into a higher risk category. The remaining risks, i.e., those that fall outside your risk appetite, can then be prioritised and managed accordingly.
Closing Thoughts
Effective information security risk management is about making informed, proportionate decisions that protect what matters most. You don’t need to eliminate every potential issue; the goal is to build clarity around your assets, the risks that could affect them, and the level of risk your organisation is willing to tolerate. With that understanding, risk treatment becomes a practical, targeted process that supports sensible and defensible decision making, rather than an overly complex or resource intensive exercise.
How URM Can Help
Having supported hundreds of organisations’ information security risk management programmes over the course of 2 decades, URM is the ideal partner to help you create and implement an effective information security risk management plan. With our proven information security risk management software, Abriska 27001, we can support the entire risk assessment process, including assistance with treatment. Our team can help you prioritise treatment activities to maximise your time, effort and budget, as well as supporting the design and implementation of information security controls and measures that are fully aligned with your organisation’s unique style and needs.
If your goal is to certify against ISO 27001, the world’s leading information security information security management system (ISMS) standard, URM can draw upon the experience gained from 400+ ISO 27001 certification projects (and not a single failure) to support you. Our experts can assist with all stages of the Standard’s lifecycle, from conducting an ISO 27001 gap analysis and guiding ISMS implementation, through to supporting post-certification conformance with ongoing management system and control audits.
URM can help you achieve ISO 27001 certification
Unsure whether your ICT risk framework meets DORA standards? Our experts will carry out a detailed gap analysis and provide clear, prioritised steps to help you achieve full compliance.
Our consultants will evaluate your organisation against DORA’s core requirements. Gain practical insights to strengthen your digital resilience and meet regulatory expectations.

URM’s blog explains the building blocks of information security risk, outlining how risks can be valued and prioritised, the role of rise appetite, and more.

URM’s blog offers key advice on implementing the physical controls in Annex A of ISO 27001 and preparing for a successful physical controls audit.



